RESILIENT EDGE STACK
Hardware enforced
security, compliance & resilience
for intelligent edge infrastructure

Build Faster. Deploy with Confidence.
Faster Innovation
Integrate security at any stage of development without costly architectural rewrites. Deploy updates confidently and iterate faster—without disrupting operations or risking bricked devices.
Reliable Operations
Maximize fleet ROI with higher uptime and faster recovery. Automatic rollback and recovery endpoints restore devices to a verifiable state—eliminating costly truck rolls and manual intervention.
Secure & Compliant
Meet NIS2, EU CRA, and industry standards with hardware-enforced security, self-attestation, and recovery—designed for unattended devices operating long term in zero-trust edge environments.
Freedom to innovate. Confidence to scale.
Secure and resilient from day one

Software Defined
Core device security, ironclad updates, and self recovery in a simple unified software solution.
Hardware Enforced
Get protection fast with plug-on modules, then optimize at scale with chip-down solutions for OEMs

Rapidly Deployed
Fully integrated enterprise grade computers ready to deploy. Easy to customize with available dev kits.

Software Stack
Core device security, ironclad updates, and self recovery in a simple unified software solution.

Security Modules
Get protection fast with plug-on modules, then optimize at scale with chip-down solutions for OEMs

Secure Edge Nodes
Fully integrated enterprise grade computers ready to deploy. Easy to customize with available dev kits.
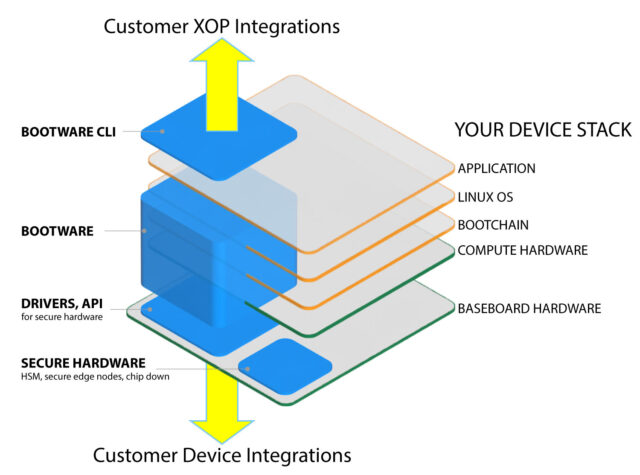
Hardware enforced device security and recovery stack
Zymbit modular security stack is robust and easy to integrate
- Secure boot integration
- File system encryption
- AB image partitions with automatic rollback
- Flexible recovery endpoint and policies for unattended devices
- Choice of secure hardware that scales to chip level integration
- APIs for easy integration with applications and XOPs tools
- Hardware security engine for cryptographic services and key management.
Trusted by professionals worldwide


Loved by developers
Modular software and hardware that scales smoothly as your device security needs grow

Trusted by ops teams
Long term security and reliability managed from your existing ops infrastructure
For intelligent edge infrastructure

Adaptive Retail
enables dynamic customer-personalized experiences, protects identity information
Factory Automation
protects valuable software IP in zero trust manufacturing environments

Drone Infrastructure
protects critical navigation and communication credentials in drones and traffic managers

On-Prem Key Management
enables application specific cryptographic key management, wallets and services

Diagnostic Equipment
protects sensitive information, enables out of band service access for high availability

Agrotech
supports encrypted file system, robust OTA updates and self-recovery