If all software, including security software, runs on hardware, then what secures the hardware?
All software runs on hardware!
Many software engineers enjoy the convenience of running software in a container, on a virtual machine, in some distant physical machine. The burden of allocating, managing and securing hardware, operating systems and service patches is someone else’s problem, by design.
This model of hardware abstraction works well for SAAS platforms and enterprise based applications that rely upon third party cloud vendors or in house IT teams to take care of the operational details. Extending the model to attended devices such as personal computers and mobile devices that are physically beyond the secure perimeter is challenging, but effective solutions are available and used widely. Extending the model to unattended assets that are widely distributed is even more challenging and, for reasons we will explore in this articles, are in need of effective solutions.
Securing hardware
Security is an not an absolute science. The level and types of security vary widely depending on the use case and threat model. But in all cases, effective security relies upon hardware that is physically secured and supported by dedicated cryptographic hardware.
Lets review a few examples.
Secure hardware in data centers
Enterprise grade server hardware is generally secured to the highest standards, which makes securing a typical data center both complex and expensive.

Effective security is achieved through a combination of physical, technical and administrative controls(1).
- Physical controls – fences, buildings, security cameras, door locks, biometric scanners, server cages. Watch Google’s six layers of physical security in action.
- Technical controls – identity and authentication solutions, firewalls, antivirus software, intrusion detection and protection systems, access control lists, encryption measures, cryptographic key generation, storage and management.
- Administrative controls – policies, procedures, or guidelines that define personnel or business practices. Security awareness training, procedures for employee hiring, termination and equipment usage. Organizational design and separation of duties.
Together these controls form a multi-layered secure perimeter, and it’s reasonable to assume that all hardware inside the perimeter is very secure.
Secure perimeter & zero trust model
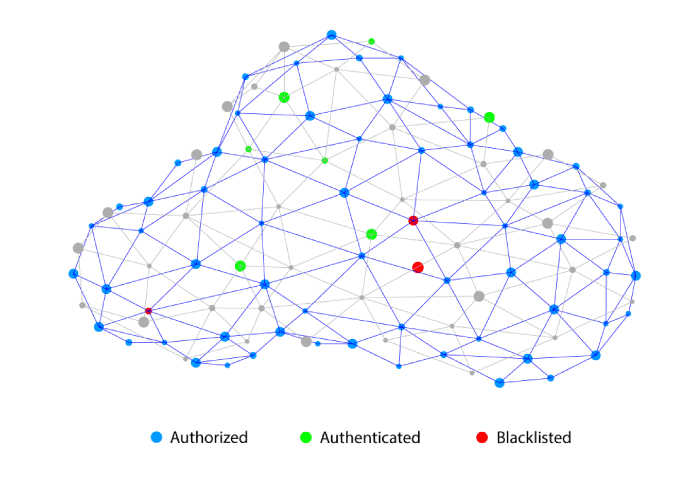
The boundary of this secure and managed hardware space is known as the Secure Perimeter. Everything inside the perimeter is nominally considered ‘secure and trustworthy’ and everything outside the perimeter – clients, end points, edge devices, iot devices, machines, etc – is considered non-trustworthy, until proven otherwise. This zero-trust security model is common-place today.
Identity, authentication and access
The action of authorizing access to authenticated clients only is a simple idea to understand, but effective implementation is more complex. Modern expectations require that every client (thing or user) has a unique, unclonable identity that can be authenticated quickly, from anywhere on the planet, and then subsequently authorized to access only certain pre-approved resources.
Cryptography and key management hardware provide the technical foundation for verifying identity and integrity, while authentication services from vendors like Okta and Duo provide the application layer that simplifies access controls for billions of clients.
The critical role of access controls is demonstrated by the the market size for identity and auth. services which Okta estimates at $80Bn.
Cryptography & key management are the foundation of modern security
Without diving into the details, its sufficient to say that modern cryptography is mathematical magic that is provably and measurably (by smart cryptographers) secure to some threshold of exploits.
Cryptographic algorithms are used to encrypt, sign and verify data sources. They can prove that a party ‘owns’ certain information, without requiring knowledge of that information – zero knowledge proofs – which is important in preserving the privacy of sources. And they are increasingly important in the growing decentralized digital economy being built around digital assets, peer to peer transactions and immutable blockchain ledgers. Learn more about cryptography.
Secure cryptographic hardware
Given the critical role of cryptography and key management, it is vitally important that the process of cryptography, key derivation, storage and management be performed within hardware that is independently secure from other hardware resources. Such secure cryptographic engines are available in different sizes, performance, algorithmic variety and complexity. Here are the major categories:
- Hardware Security Module – rack mounted device, used in data centers and servers.
- Trust Platform Module – chip or module, used in personal computers and some embedded applications.
- Secure Element / Enclave – chip or die, embedded inside SOM – system on module.
- Digital Wallet – USB plug-in, used for crypto key storage and management.
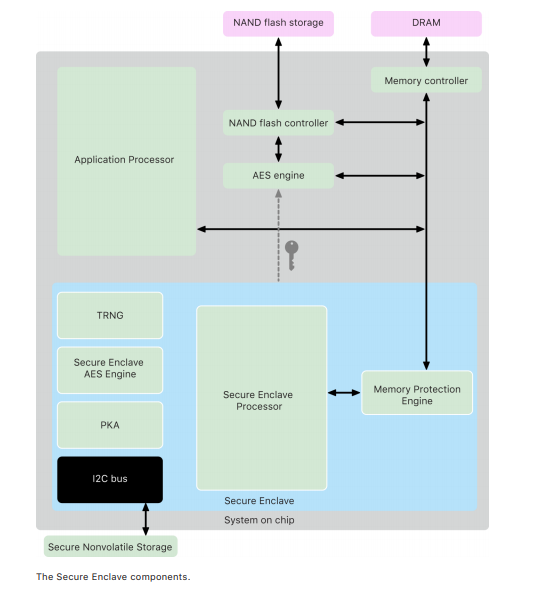
Hardware security in phones and laptops – Apple Secure Enclave
From Apple platform security model May 2021 – Learn more>
Hardware security in servers – Securosys HSM
The internet is evolving
The model we have discussed so far assumes a secure-perimeter with many servers inside and many authenticated-clients on the outside. This model generally works well for today’s internet population which is dominated by billions of client mobile devices and personal computers talking to centralized services.
Such clients have the added advantage of being largely homogeneous hardware types (Intel, AMD, Apple, Samsung, ) running a few dominant operating system types (Windows, Apple, Android). This enables the large investments in secure hardware to be leveraged across billions of devices.
But the internet is evolving (again). Everything is becoming ‘smart’ with the capacity to compute locally, connect directly to nearby resources, make autonomous decisions and approve transactions. Technologies like 5G, AI and blockchain will enable this evolution, opening the path for new business models such as asset sharing and process optimization.
Whether you call it the digital transformation, the fourth industrial revolution, or the IoT explosion, we can we sure about one thing – securing such a distributed internet will be challenging. Every thing, every asset must be capable of operating outside the secure perimeter of the cloud, autonomously with zero requirement for an attendant user. Also every thing should be able to transact securely with other peers that also live outside of the secure perimeter. How can we do this?
The need for self-secured assets with a perimeter of one
Thankfully, securing distributed assets in a decentralized internet can leverage many of the foundational technologies – if not the products – that we have already discussed.
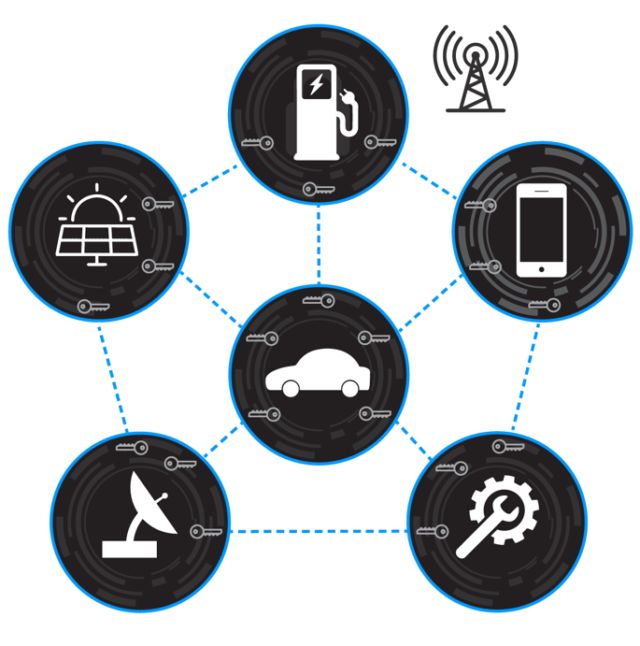
Every thing must carry its own hardware based cryptographic engine to create an identity, encrypt local digital assets, support secure peer to peer transactions and provide local authentication services. Sensitive hardware must be protected inside a self-secured ‘perimeter of one’ which provides resilience against both physical and digital exploits.
The future connected-vehicle is a good example of how such self-secured assets must operate and interact with their environment, irrespective of whether they have connection to centralized services. Standards for such V2X (vehicle to everything) services are evolving, along with new business models for asset sharing, precision insurance and retail selling.
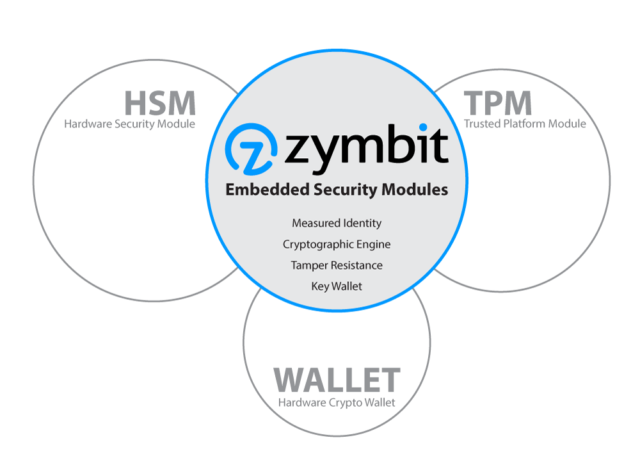
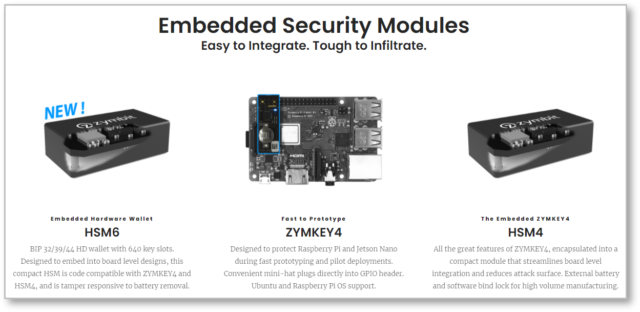
Zymbit Embedded Security Modules
To address the unique requirements of self-secured assets, Zymbit has developed a series of embedded security modules that combine some of the important attributes of TPM, HSM and wallet class cryptographic engines.
Core features of Zymbit embedded security modules are:
- Robust measured identity, authentication and access controls.
- Secure tamper responsive perimeter.
- Cryptographic engine with independent agency and agility.
- Key generation, storage and wallet management.
- Autonomous, unattended operation.
- Easy to integrate hardware with unified software API.
Takeaways
- All software runs on hardware and that hardware needs to be secured.
- The internet is evolving into something more decentralized with billions of distributed assets.
- The secure-perimeter zero-trust model can be applied to each individual distributed asset.
- New cryptographic technologies for self-identity, zero knowledge proofs and blockchain will enable self-secured assets and autonomous transactions.
- A new class of embedded security modules is required to address the needs of strong identity, agile cryptographic engine and unattended operation.