Secure Compute Module
All-in-one secure Linux compute module for developers of IoT devices and infrastructure.
The hardened Raspberry Pi compute module for zero-trust environments.
Open for developers. Hardened for life on the edge.
- Raspberry Pi CM4 compute
- Secure boot
- Encrypted file system
- Hardware cryptographic engine
- Fully encapsulated, tamper resilient
- Standard and custom images
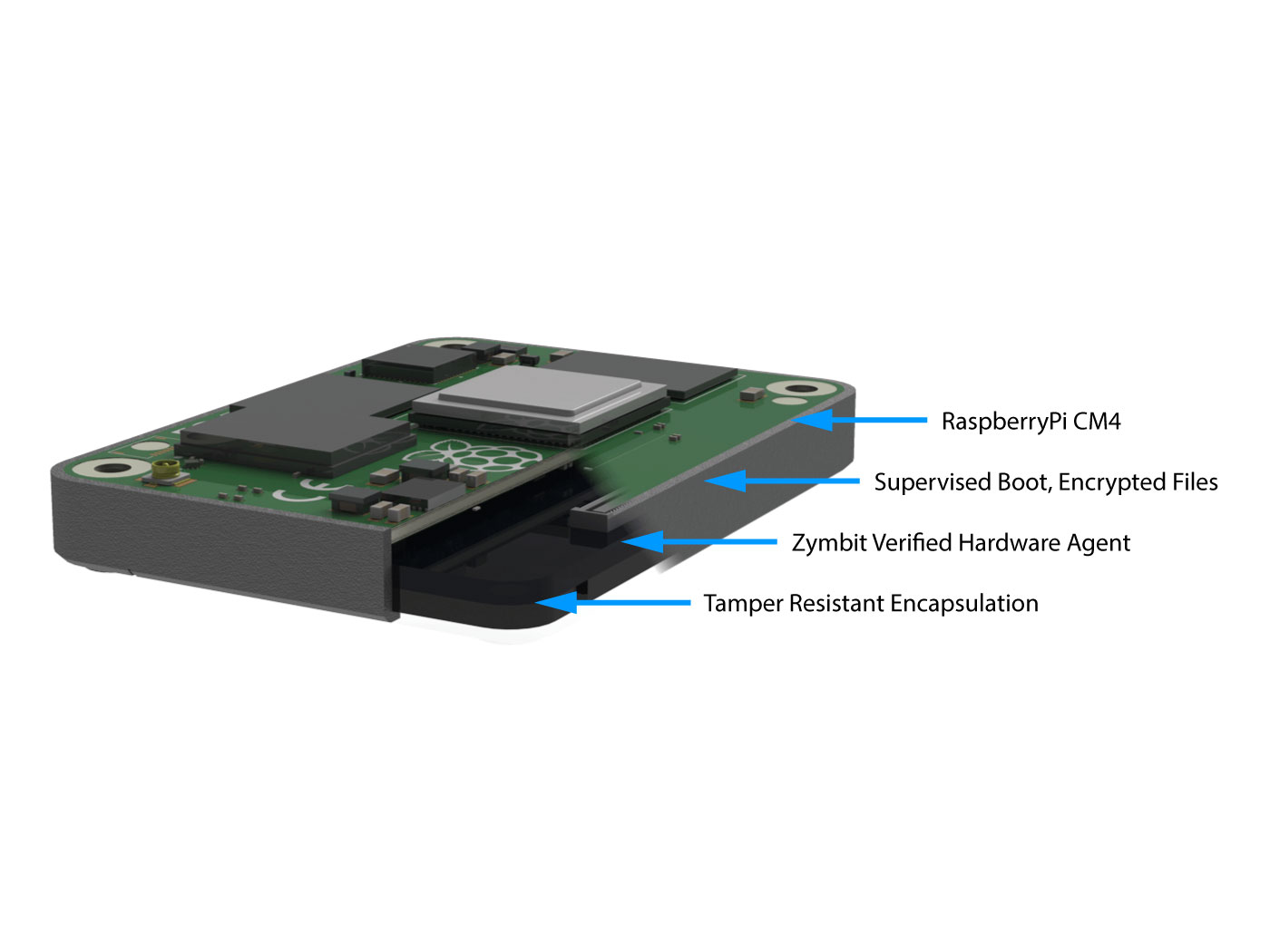
Overview
Hardware secured compute for critical applications
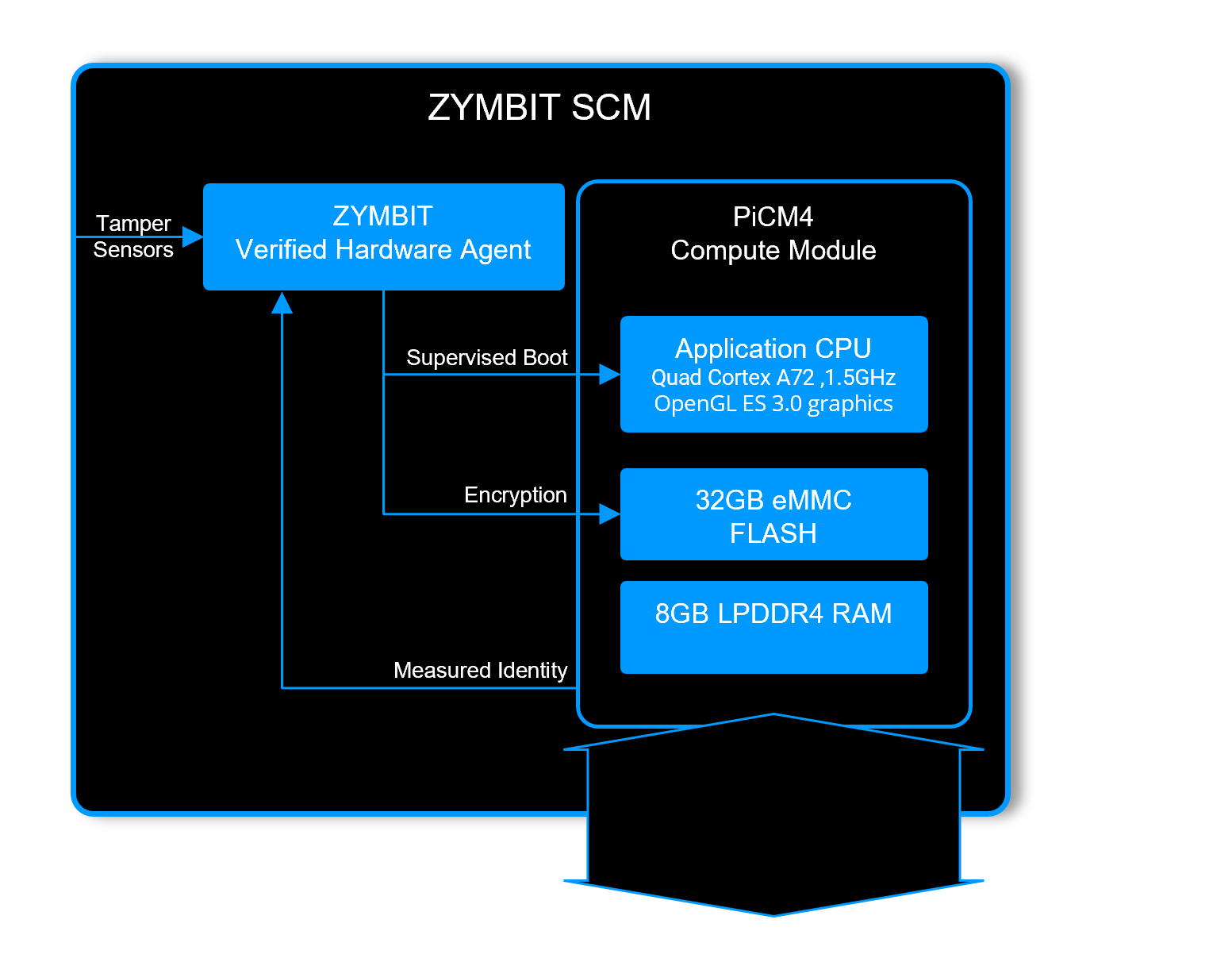
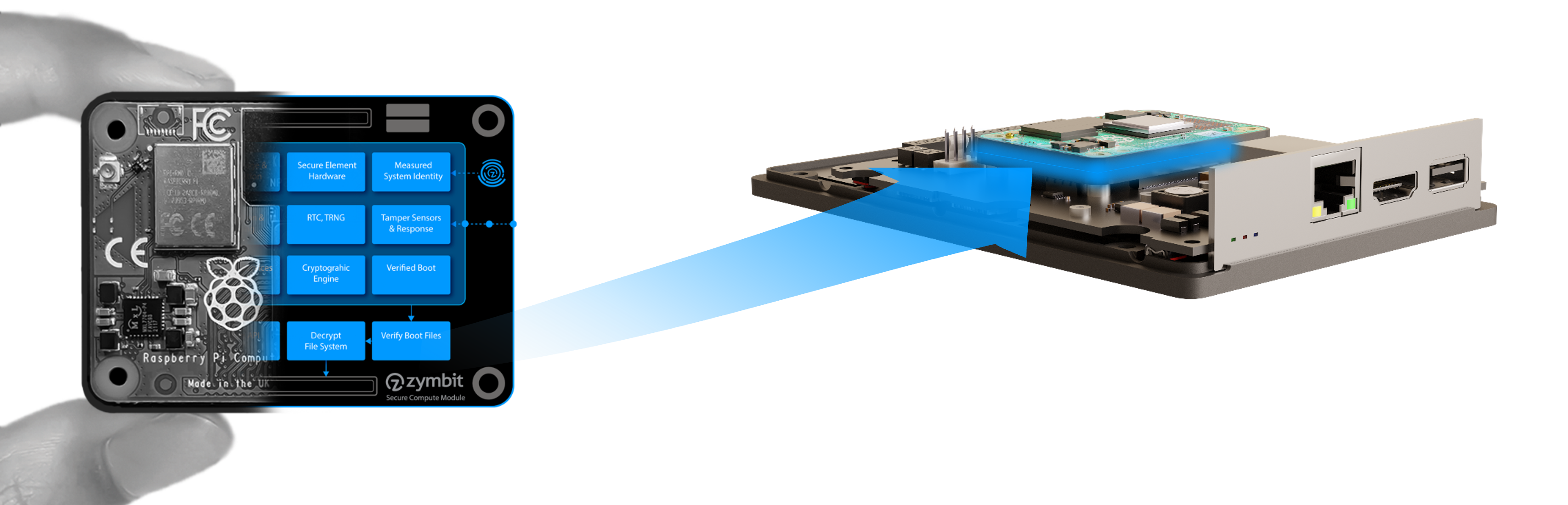
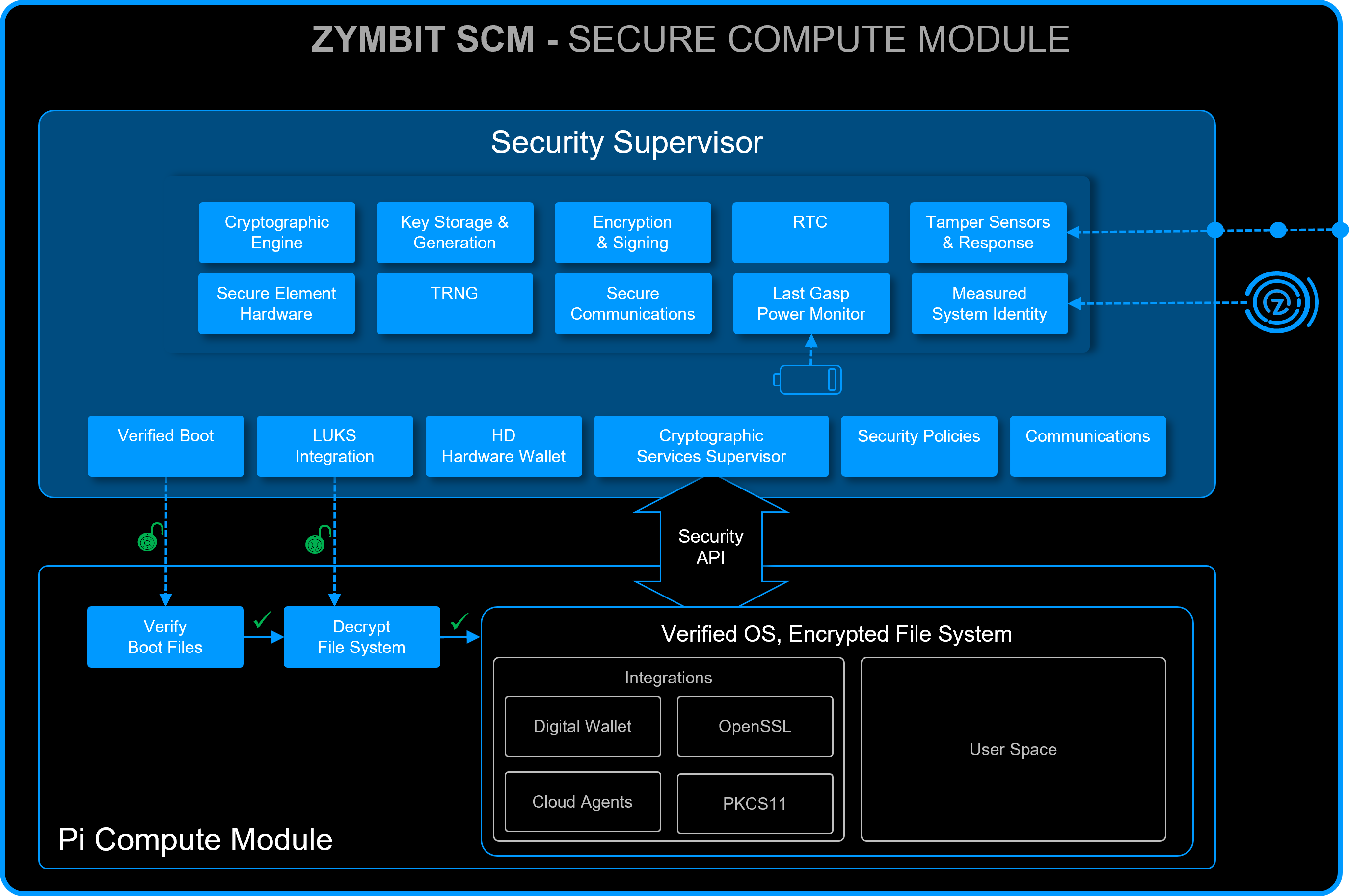
Zymbit Verified Hardware
Each SCM includes a PiCM4 compute module that is protected by a Zymbit Verified Hardware Agent. The agent runs autonomously from the CPU and provides independent verification of boot, file system access and overall system integrity.
Verified Highlights
- Secure boot on raspberry pi
- Measured system identity
- File system encryption
- Physical tamper sensors
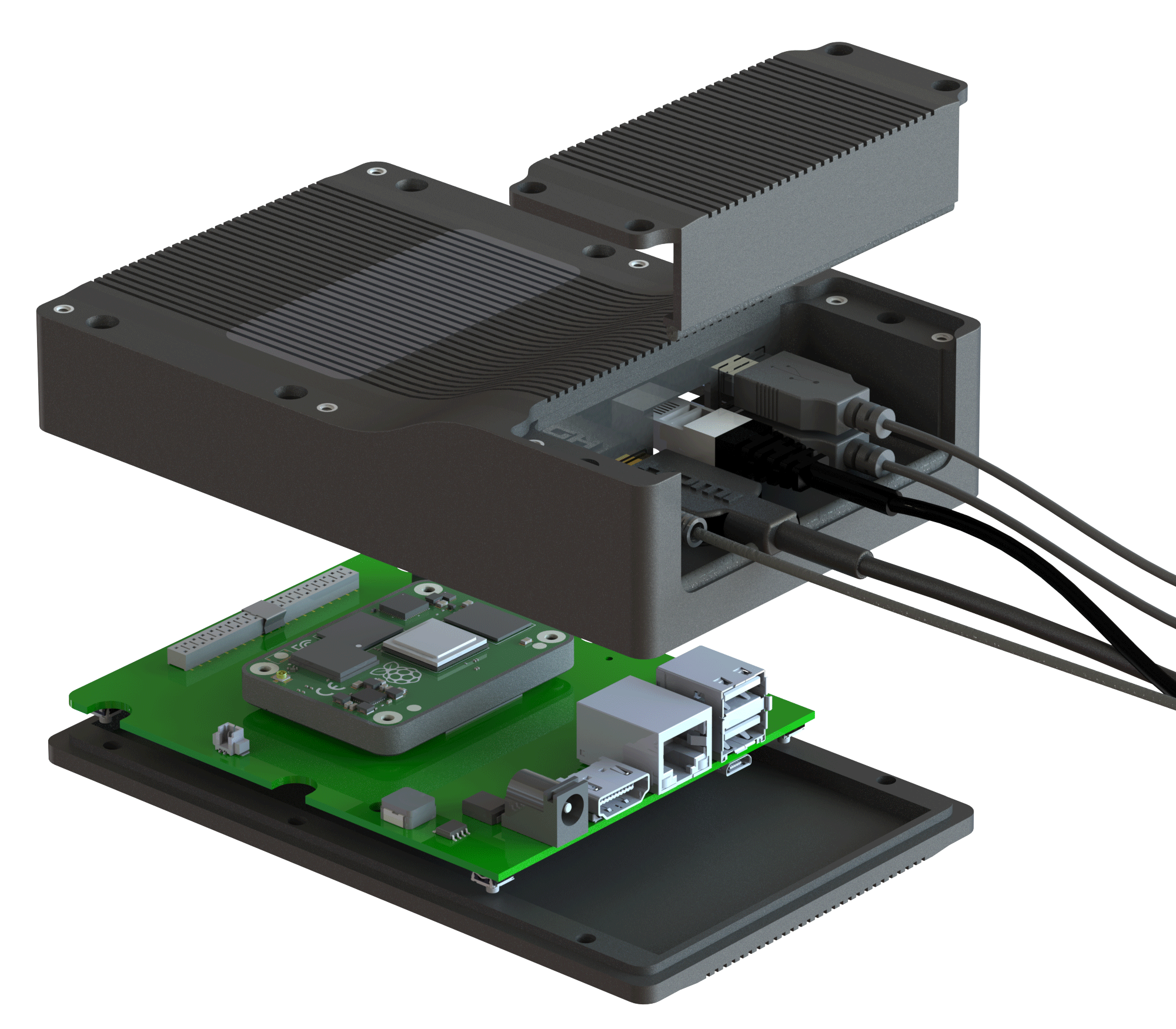
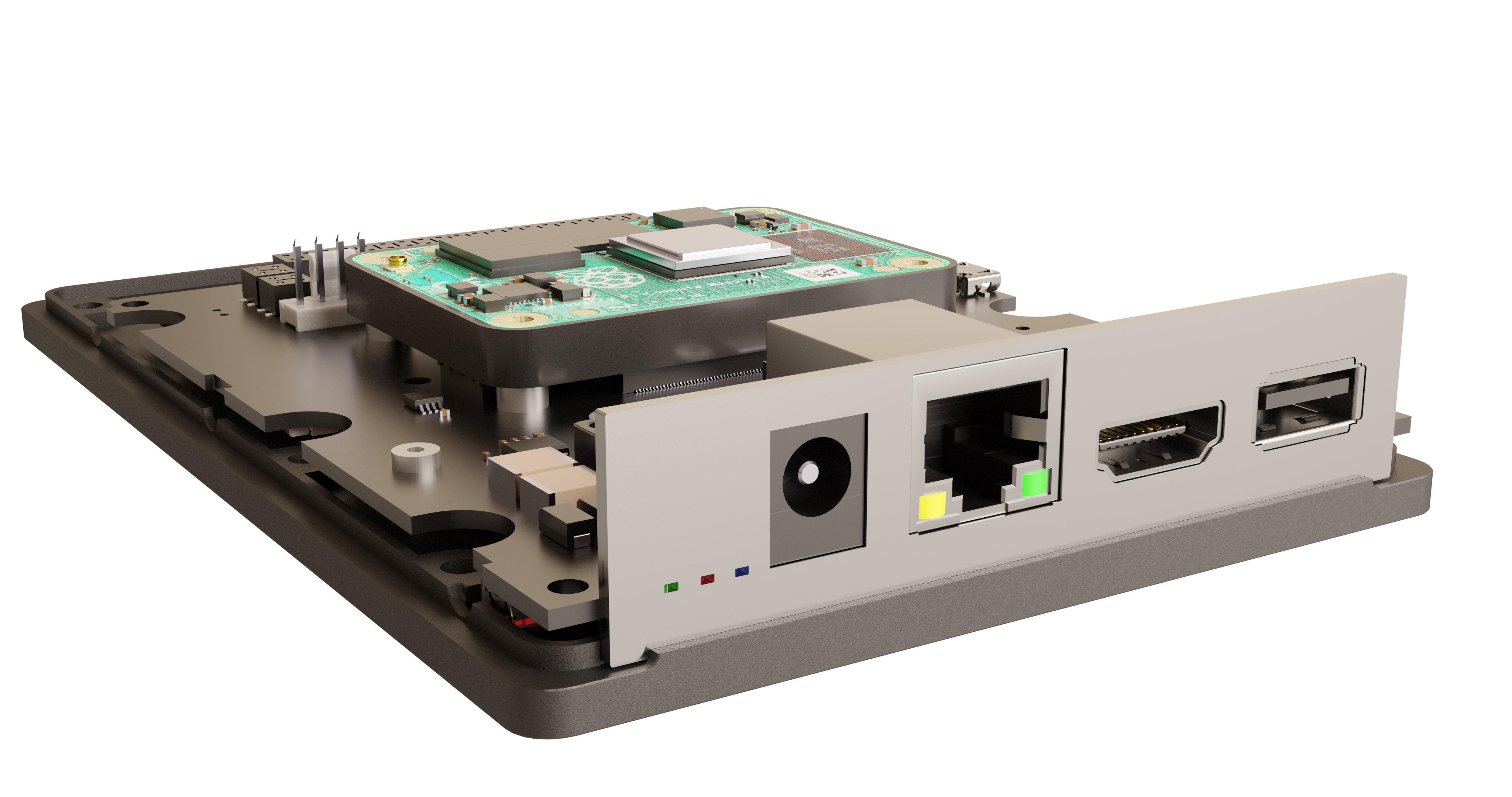
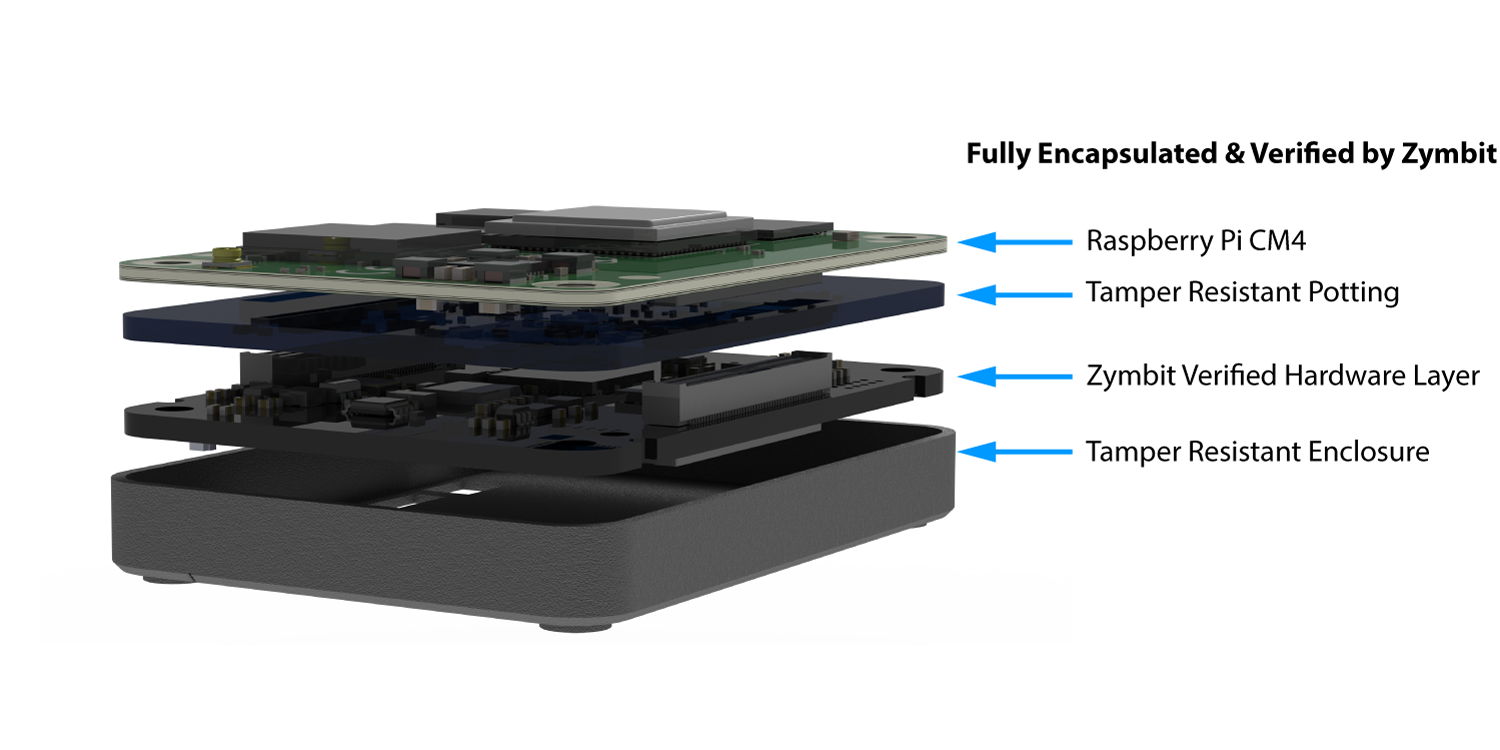
Secure encapsulated hardware stack
- Reduced attack surface, increased security
- All connections hidden
- External battery, under module option
- Internal last-gasp destruction mode

Full spec compute module
SCM includes the powerful PiCM4 Linux compute modules.
- Broadcom BCM2711 quad-core Cortex-A72 (ARM v8) 64-bit SoC @ 1.5GHz
- H.265 (HEVC) (up to 4Kp60 decode), H.264 (up to 1080p60 decode, 1080p30 encode)
- OpenGL ES 3.1, Vulkan 1.0
- Up to 8GB LPDDR4-3200 SDRAM
- Up to 32GB eMMC Flash memory
First release product leverages the resources of the PiCM4 family of compute modules.
- Broadcom BCM2711 quad-core Cortex-A72 (ARM v8) 64-bit SoC @ 1.5GHz
- H.265 (HEVC) (up to 4Kp60 decode), H.264 (up to 1080p60 decode, 1080p30 encode)
- OpenGL ES 3.1, Vulkan 1.0
- Up to 8GB LPDDR4-3200 SDRAM
- Up to 32GB eMMC Flash memory
Comprehensive peripherals support
- Gigabit Ethernet, IEEE 1588 precision time protocol
- Optional 2.4 GHz and 5.0 GHz IEEE 802.11ac wireless, Bluetooth 5.0, BLE
- 28 x user GPIO configurable for
- SPI, I2C, UART, ADC, DAC, PWM, I2S
- 2 x HDMI 2.0 ports (up to 4kp60 supported)
- 1 x MIPI DSI Serial Display
- 1 x MIPI CSI-2 Serial Camera
- 1 x PCIe 1-lane Host, Gen 2 ( 5Gbps )
Python, C, C++ APIs
As developers ourselves, we try to build APIs that allow you to benefit from the power of cryptography, without needing to understand the underlying math. Zymbit wallet functions are designed to provide access to powerful features like generating a wallet master seed, child keys and managing wallet recovery from mnemonic phrases and shared secrets.
Cryptographic Engine & Services
The Secure Compute Module provides a wide choice of cryptographic services and types that are easily accessed through the Zymbit API.
Services
- Key generation and storage
- Encryption, signing and hash functions
- True random number generator (TRNG)
Cypher Suite
- ECC KOBLITZ P-256 (secp256k1)
- ED25519, X25519
- ECDH (FIPS SP800-56A)
- TRNG (NIST SP800-22)
- ECC NIST P-256 (secp256r1)
- ECDSA (FIPS186-3)
- AES-256 (FIPS 197)
Developer tools
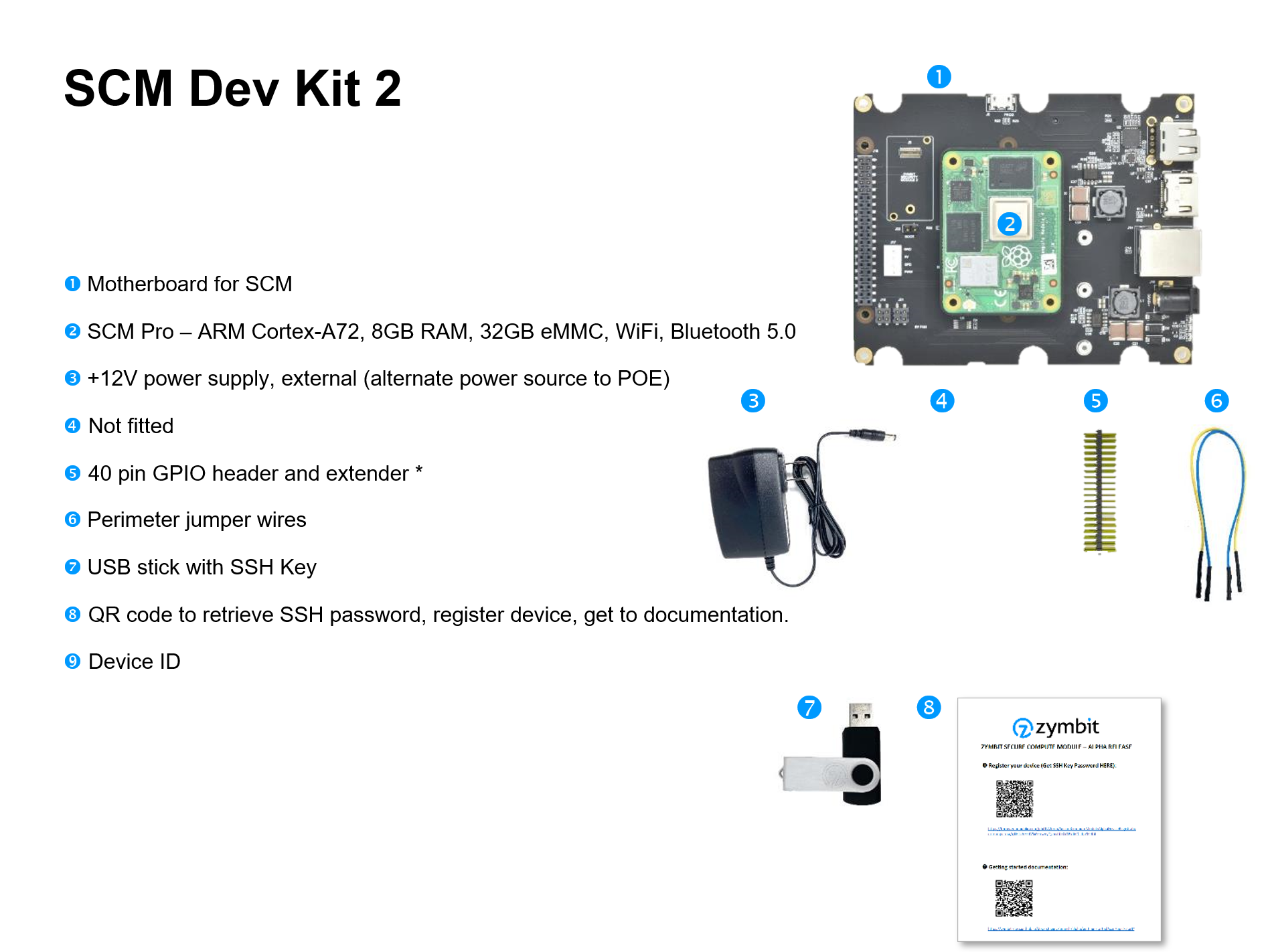
Dev Kit
- Zymbit Secure Compute Module (Integrated Pi CM4)
- Motherboard for SCM
- Perimeter Detect breakout cable
- External battery breakout
- 12V power supply
- USB drive with SSH keys necessary for SSH login
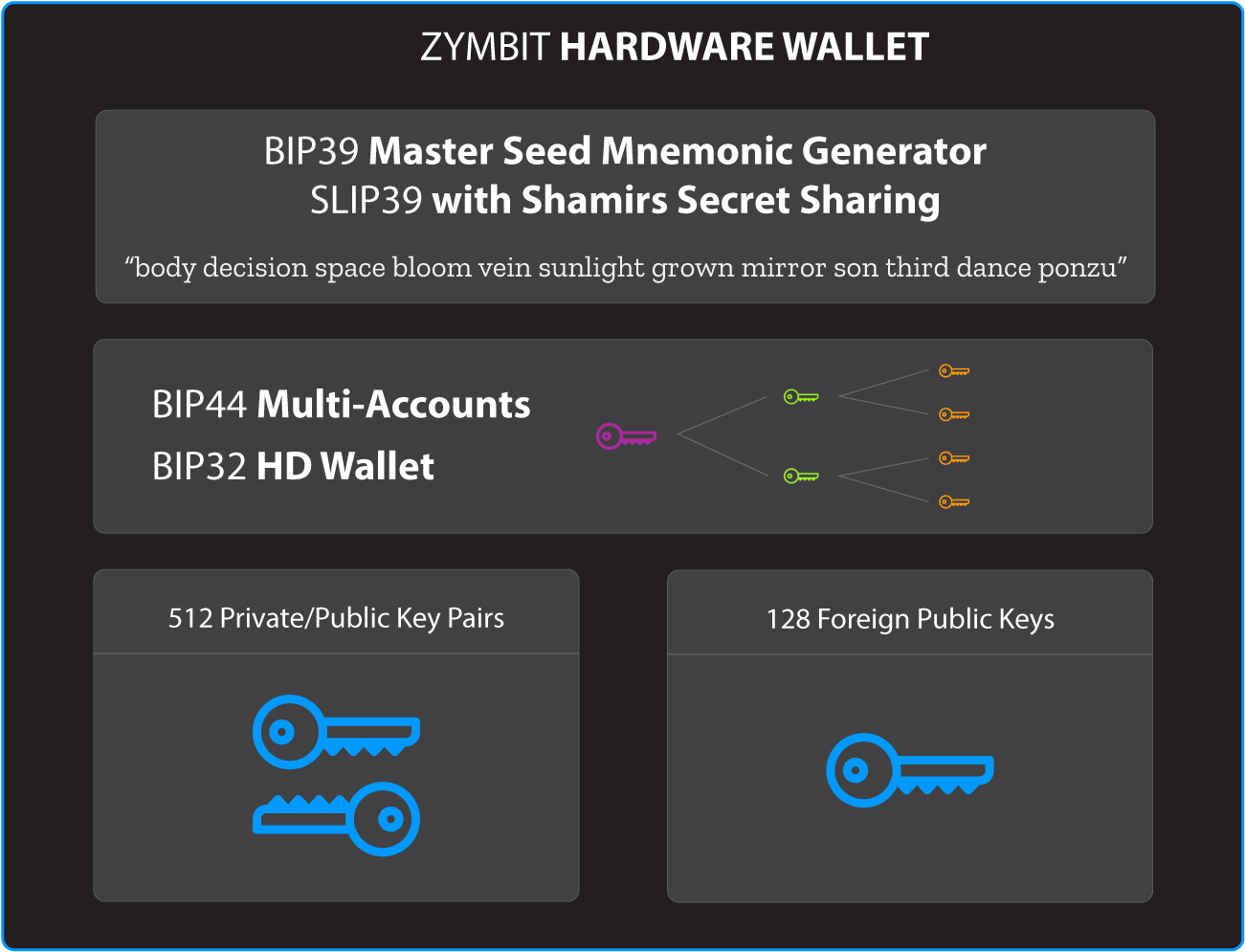
Optional HD Hardware Wallet
A Hierarchical Deterministic (HD) wallet is a reliable and secure way to manage hundreds of keys, embedded in a single device.
HD wallets use proven de-facto standard algorithms developed for blockchain and crypto applications. Zymbit’s HSM6 product implements standard protocols – BIP32/39/44 and SLIP39 – in a compact, easy to integrate module that’s programmable through secure APIs.
Tutorials on using HD wallet:
Footprint compatible with CM4
Ready to embed into your custom design
- PCB footprint, schematic symbol, 3D models
- Altium Designer & CircuitStudio
- KiCAD
- Mechanical drawings
- CAD documents >
Pre-configured the way you want
To simplify your life, the SCM can be shipped with a choice of pre-configured OS, application software and security policies that align with your product development stage.
Develop
- Optimized for maximum development flexibility
- Standard OS builds & tools
- Partially encrypted file system
- Relaxed security policies, open ports
Secure
- Defined security policies enabled
- Optimized OS build
- Fully encrypted file system
- Supervised boot configured
- Finalize configuration with Security Sanitization Guide and Scripts.
Deploy
- Customer-specific configurations loaded, tested, deployed.
- Standard zymbit curated configurations available.
Manufacturing tools and support
Zymbit manufacturing tools and services help you transition your SCM based design to volume manufacturing quickly and securely.
Specifications
| Security Highlights | Secure boot on Raspberry Pi File system encryption Key generation, storage and management in secure hardware Cryptographic engine |
| Compute resources | Broadcom BCM2711 quad-core Cortex-A72 (ARM v8) 64-bit SoC @ 1.5GHz H.265 (HEVC) (up to 4Kp60 decode), H.264 (up to 1080p60 decode, 1080p30 encode) OpenGL ES 3.1, Vulkan 1.0 Up to 8GB LPDDR4-3200 SDRAM Up to 32GB eMMC Flash memory |
| Compute interfaces | Gigabit Ethernet, IEEE 1588 precision time protocol 2.4 GHz and 5.0 GHz IEEE 802.11ac wireless Bluetooth 5.0, BLE 28 x user GPIO configurable for SPI, I2C, UART, ADC, DAC, PWM, I2S 2 x HDMI 2.0 ports (up to 4kp60 supported) 1 x MIPI DSI Serial Display 1 x MIPI CSI-2 Serial Camera 1 x PCIe 1-lane Host, Gen 2 ( 5Gbps ) 1 x USB 2.0 port ( highspeed ) |
| Private / public key pairs | 512 |
| Foreign public keys | 128 |
| Wallet Functions | BIP 32 - hierarchical deterministic wallet BIP 39 - master seed mnemonic generator SLIP 39 - with shamir's secret sharing BIP 44 - mulit-account support |
| Cryptographic Services | ECC KOBLITZ P-256 (secp256k1) ED25519, X25519 ECDH (FIPS SP800-56A) TRNG (NIST SP800-22) ECC NIST P-256 (secp256r1) ECDSA (FIPS186-3) AES-256 (FIPS 197) |
| Tamper Sensors | 2 x Perimeter breach detection circuits Accelerometer shock & orientation sensor Main power monitor Battery power monitor battery removal monitor |
| Software API | Python, C++, C |
| Physical Format | Encapsulated module |
| Dimensions | 57.2 x 42.5x 9.5 mm 2.25 x 1.67 x 0.37 Inches |
| Connectors |
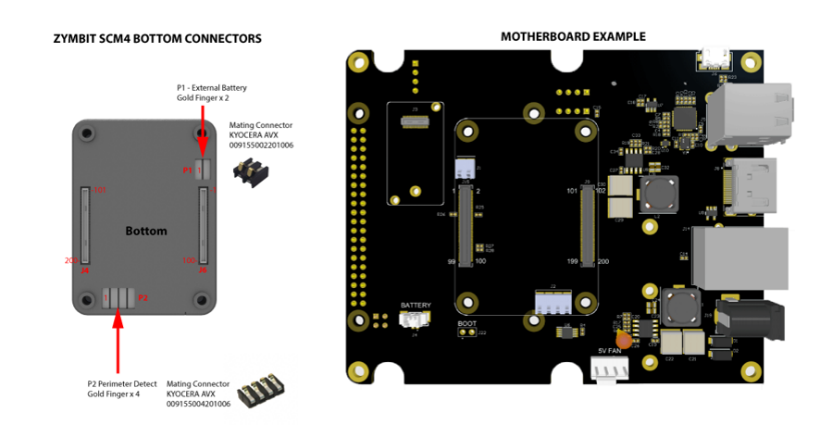
Module main connectors: 2x Hirose Header DF40C-100DP-0.4V Mating main connectors: 2x Hirose Receptacle DF40C-100DS-0.4V, 1.5mm clearance Mating main connectors, extended** : 2x Hirose Receptacle DF40HC(3.0)-100DS-0.4V, 3.0 mm clearance Mating external battery connector: 1x KYOCERA AVX 009155002201006 Mating perimeter, LED connector: 1x KYOCERA AVX 009155004201006 ** required if CR2412 battery fitted under module |
| Production mode lock | Software API command |
| Measured system identity & authentication | Standard factors include RPI host, Zymbit HSM, eMMC memory |
| Data encryption & signing applications. | Encrypt root file system with dm-crypt, with LUKS key manager hook Encrypt data blobs with "zblock" function Encrypt data in flight with OpenSSL integration |
| Real time clock | 36-60 months operation with external CR2032, application dependent, 5ppm accuracy. |
| Backup battery | Used for RTC and perimeter circuits Under-module battery connector pads, to any 3V source on motherboard Optional under module battery holder, for CR2412 coin cell * * requires motherboard connector height 3.0mm |
| Backup battery monitor | Yes |
| Last Gasp battery removal detection | Yes |
| OEM Custom features | Contact Zymbit |
| Example Cipher Suites | AWS-IOT | TLS_ECDHE_ECDSA_AES256_SHA MS-AZURE | TLS_ECDHE_ECDSA_AES_128_GCM_SHA256_P256 |
| Accessories & related products | Developer Kit |
| Warranty | 18 months |
Documentation
Using Product >
- Getting started
- Software APIs – python, C, C++
- Tutorials
- FAQ & troubleshooting
Conformity Documents >
- EU Declaration of Conformity
- FCC Declaration of Conformity
- RoHS/Reach Declaration of Conformity
- California Prop 65 Declaration of
CAD Files >
- Mechanical dimensions
- Step model
Manufacturing Tools >
- Secure high speed encryption appliance
- Programming and provisioning