Embedded digital assets deployed in the wild are vulnerable to cyber and physical exploits.
Key considerations
- Physical assets with embedded digital content are often deployed in the wild, beyond the security of a data center.
- Defining WHO is responsible for securing these edge assets is an obvious first step, but one that is often deferred.
- Undetected access to edge compute devices makes digital assets highly vulnerable.
- Key credentials, software IP and critical process data can be easily exposed without detection.
- The impact of breaching a five dollar SD card can easily run into millions of dollars, even loss of life.
- Physical access exploits also can include intercepting open wireless communications at short range.
- Every physical asset should be uniquely identifiable, provisioned and managed.
- Management of these devices should be consistent with and integrated into existing enterprise security frameworks and functions.
First think and get organized
Many operational assets have been deployed outside the security of a data center and the purvue of IT management. The responsibility for securing these ‘edge assets’ is often unclear within an organization; should development, operations, IT or maintenance take the lead? Getting clarity on this responsibility is an important starting point. Upcoming legislation and showcase criminal negligence trials are sure to drive closer attention in coming years to this important organizational factor .
____________________________________________________________________________________________________________________
Life in the wild is very different from a secured data center
A typical data center security schema might look like this one at DataFoundry’s Houston 2 facility.
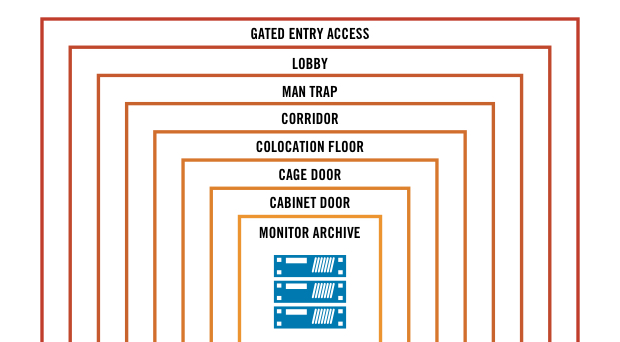

Images courtesy of DataFoundry’s blog.
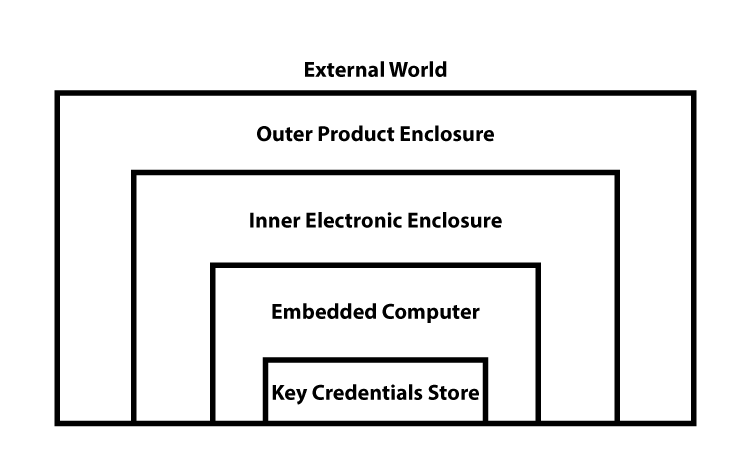
In contrast, the security schema for a a typical edge asset might look like this EV charging application: The asset is physically accessible, easy to exploit, yet likely unattended for extended periods of time.

(Stock photo, actual design unknown)
For an asset like this we would hope to see several layers of physical access controls with tamper detection protecting the outer and very inner layers.
Often it’s most instructive to consider the value of the commodity or utility transacted by the edge asset. This can be many times the face value of the underlying asset. In other cases the value is in the data collected by the assets, or a proprietary algorithm, or simply the keys and credentials to upstream digital services and assets.
Don’t waste too much time asking WHY someone might want to compromise your edge device. Someone will – whether a lone hack, state actor or cyber terrorist – it’s just a matter of when and how. Do spend your time considering what the impact of that breach could be and what mitigation you can build into your product design upfront. Cleaning up after the fact can be painful or lethal to your organization, especially if best and obvious practices were not followed.
____________________________________________________________________________________________________________________
Anatomy of CyberPhysical exploits
Medical Device Exploit
On March 21, 2019, the US Department of Homeland Security reported a vulnerability in the Medtronic Conexus Radio Frequency Telemetry Protocol, impacting medical devices.
This is an example of a wireless exploit that took advantage of close promixity and lack of a basic authentication of authorization protocol within the devices.

“The Conexus telemetry protocol utilized within this ecosystem does not implement authentication or authorization. An attacker with adjacent short-range access to an affected product, in situations where the product’s radio is turned on, can inject, replay, modify, and/or intercept data within the telemetry communication. This communication protocol provides the ability to read and write memory values to affected implanted cardiac devices; therefore, an attacker could exploit this communication protocol to change memory in the implanted cardiac device.”
Card Exploit
Learn how to encrypt an SD card >
Many single board computers use a microSD memory card. This is easily removable, by design, for the convenience of developers and manufacturing. Unfortunately this convenience is also on offer to hackers. Within just a few minutes, they can easily remove the card, clone and or modify the contents, then re-insert – without detection.

This attack vector can be mitigated by encrypting the SD card with device unique credentials, such that a cloned copy cannot easily be decrypted on another system under the attackers control and timeline. An additional layer of physical tamper detection can significantly raise the barrier to an attack – as it slows the timeline and lowers the chances of successfully removing and re-installing an SD card.
Critical infrastructure companies and the global cybersecurity threat. McKinsey Article, April 2019
Read McKinsey report >
Operational technology assets that are remote and physically exposed will require careful attention to Identity and Access Managament (IAM) policies. Authorized logical and physical access is required by good actors for installation, field service and lifecycle management. Such access controls must provide for local (physical) access and remote (network) access.

Exposure to third-party risk:
“The electricity, oil-and-gas, and mining sectors have been rapidly digitizing their operational value chains. While this has brought them great value from analysis, process optimization, and automation, it has also broadened access to previously isolated ICS and SCADA devices by users of the IT network and third parties with physical and/or remote access to the OT network. In many cases, this digitization has allowed access to these OT devices from the wider internet, as well. “
____________________________________________________________________________________________________________________
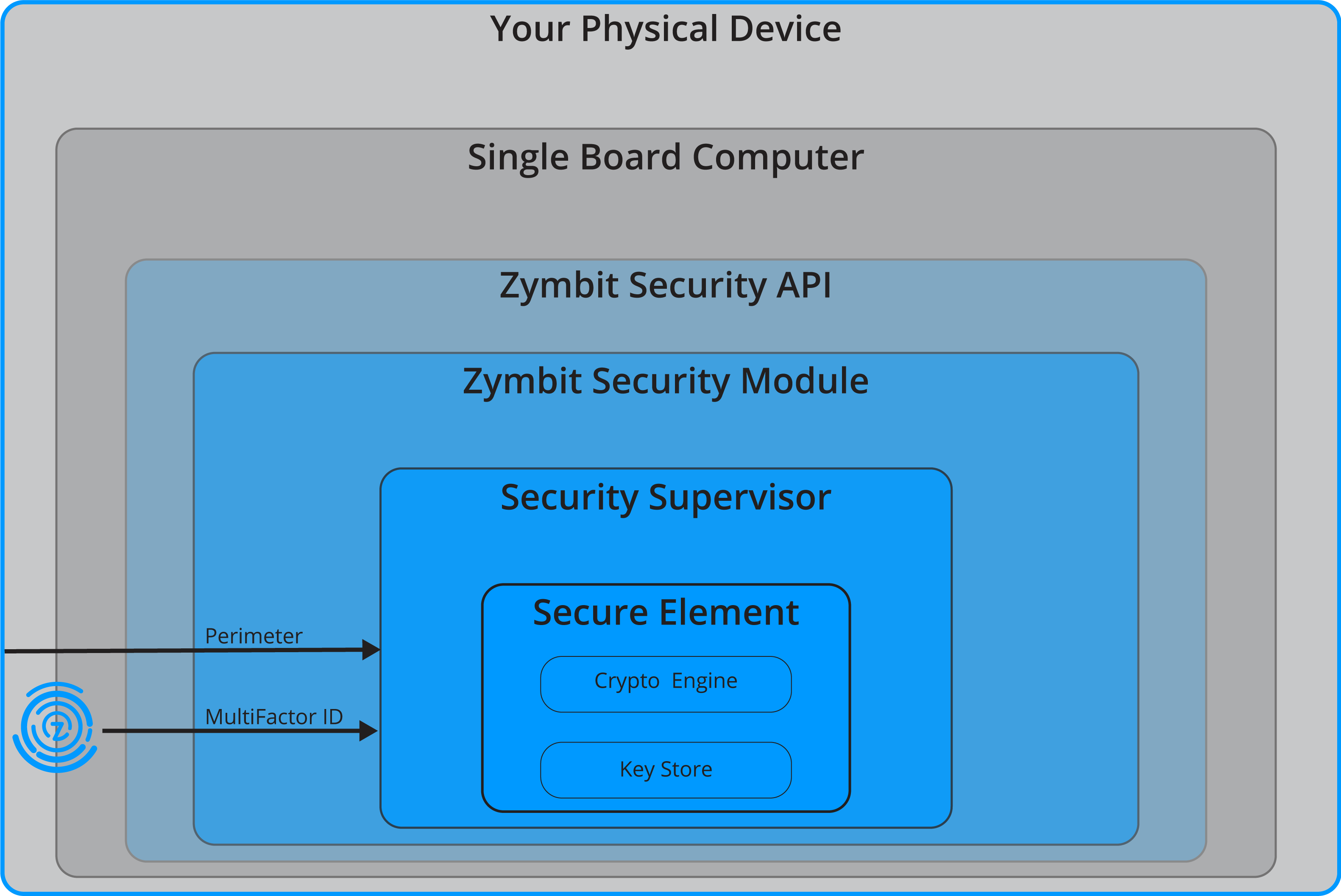
Zymbit CyberPhysical Security Solutions
Zymbit products are designed with a layered architecture that delivers both cyber and physical security – sometimes called ‘defense in depth’. Our modular security products are designed to work with popular single board computers, providing file encryption, physical security, a measured device identity and secure cryptographic engine. These layers of defense work together seamlessly to extend the security envelope from cloud service to sensors.
Learn more about Zymbit solutions> >
____________________________________________________________________________________________________________________




